Background:
Lightshot is a utility for Windows and Macs that allows you to take screenshots of select portions of your screen. It's handy if you don't want to use the built in Windows function which is honestly lacking. Personally I recommend Greenshot.
How the campaign works:
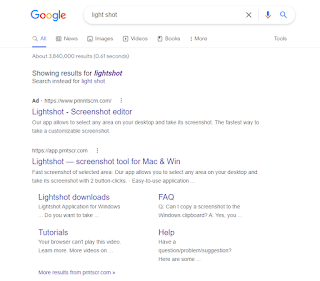
Honestly, this is well put together. The attackers paid money to get this to be the first result on Google through advertisements. See below:
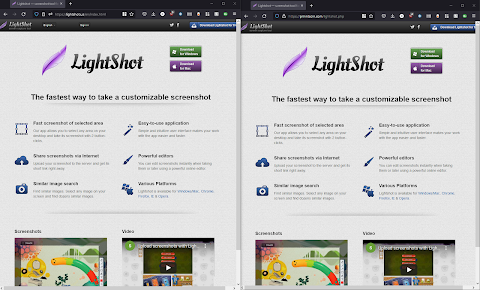
And if you go to the website, I can't blame people for not being able to tell the difference:The image on the right is the fake site, well built to mimic the real one on the left. And if you download the fake version, you actually do get Lightshot installed, but also an old NetSupport client compiled in 2009:
Examining the installer:
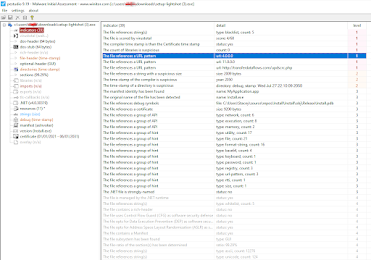
If we take a look at the installer in PEStudio, we can see a number of red flags. First, the code was compiled in 2050 - why this is a red flag is self explanatory. Next, it has 0 imports. This suggests that files are imported at run time in order to make static analysis more difficult. Also, the file has a reference to a URL which we'll see utilized below to send some initial information. Finally, the PE has unusually high entropy which indicates that it has packed data.
What the malware does:
When you launch the installer, Lightshot sends out a POST containing your private IP:
Once you have Lightshot installed on your PC, a number of actions follow. First, you'll notice that Net Support is installed under C:\Users\Public\support, which is a common location for files trying to hide. Then you have a new registry key created for persistence with support.exe:Then, Support.exe starts attempting to phone home:
After phoning home, the attack becomes hands-on-keyboard. Support.exe receives a remote connection from the attacker and a DLL is copied over. Then through remcmdstub.exe, NetSupports tool for running commands, this is run: remcmdstub.exe 1992 1804 2000 2004 %COMSPEC% & remcmdstub.exe 1992 1804 2000 2004 %COMSPEC%
Which spawns: "C:\Windows\System32\rundll32.exe" "c:\Intel\6789341.dll"
This DLL that is attempted to run is a Cobaltstrike beacon. Once ran, antivirus flagged it and stopped it from executing further, and the DLL was subsequently deleted.
Wrapping up:
It's hard for average users to stay abreast of this type of campaign when the attackers do such a good job mimicking the real site and installer, not to mention the installer is signed and verified so Windows won't throw any errors. This is made even more so when they buy ad space that manages to come before the legitimate site in searches. It's important to remember to check the URL, in this case the giveaway being the extra "n" in the URL, as this the least you can do to keep yourself protected. Up to date antivirus is also evidently important since it will stop beacons from reaching out and further compromising the system. Watching for foreign IP's can only do so much as the ones in this case were a mix of Asian and American systems. This also isn't the first time something like this has happened.
IOC:
66.29.138[.]19
103.159.132[.]236
http://transferdataflows[.]com/updscrc.php
ad49c28159f0d5a6e974e5e55518357196583dac6751cb31f2328739b326a30c - setup-lightshot
275e5b085534f64313b50cbdcb08ecd59c57d21c96bb937f140ee92a3d27f792 - NetSupport/client32